@21:01JST
Now, I’ll write the story about the title.
I tried a Puppy Linux (Precise-571JP) to use as a SHOUTcast server on a LOOX T93B. To talk about conclusions, I gave it up. I installed a Puppy Linux after a long interval. The last time I used a puppy whose version was 5.01 and English. At this time, I was very glad Precise-571JP is very easy to use. I think Puppy is one of good linux distributions. It is very light and doesn’t require high specs, nonetheless, the LOOX has too low specs.
Actually, though I could run a Shoutcast server and broadcast streams, I could never fix jumpiness even after stopping several services of Puppy’s default.
If you want to use Precise-571 as a mobile OS in a USB flash drive, I think it is very good.
Edit(Oct.10):
Ooops! I understood that the star above was not Uranus. I checked it up by StellaNavigator 10. It’s an amazing software though I used a trial version.
When I use jpegtran on Windows, it’s very inconvenient. So I made a batch file for myself, which overwrites the original jpeg file with the new optimize jpeg file.
@echo off
setlocal enabledelayedexpansion
pushd %~dp0
for %%a in (%*) do (
set OutFile=%%~na%%~xa
jpegtran -copy none -optimize -outfile !OutFile! %%a
for %%b in (!OutFile!) do set fileSize=%%~zb
if !fileSize! LSS %%~za (copy !OutFile! %%a>nul)
del !OutFile!
)
popd
exit
Bacicaly, the batch file replaces original jpeg files with new ones, but it leaves original files instead new ones when the new file is bigger than the original. This sometimes occurs if the original was created by some graphics editors. Around 100 files possible at one time. This maybe depends on cmd.exe ability itself, I think.
How to use the batch file:
- Copy & paste the above codes to a text editor, and save it as a batch file named ‘jpegtran.bat’ or something. You can have ‘jpegtran.txt’ from here. Change its extension from txt to bat.
- Copy the batch file and jpegtran.exe to the same folder.
- Drag & Drop the jpeg files you want to optimize onto the batch icon.
- That’s it.
If you use the batch file, please remember the followings. This batch file makes overwriting, so it leaves no original files.
I optimized all jpeg files in my sites. Now, I have no suggestion about jpeg files from PageSpeed Insights. Clap, clap.
References:
1. List of DOS commands (Japanese)
2. Jpegtran’s help
Edit(2016.Oct.29):
This post has a few visitors. So, I added some though I wrote this long before 😋.
You can place the folder (in which, jpegtran.exe and jpegtran.bat) anywhere in your PC. For your convenience, you should create a shortcut of jpegtran.bat on your Desktop. The shortcut ability equals jpegtran.bat itself.
You can do bulk actions for jpeg files are in some ranges by the batch file. Search jpeg files for the ranges and “Select All” then Drag&Drop.
Just before noon, I noticed I could not reach qa.php.net and the PHP 5.6.1 Zip was withdrawn from the site.
What happened to the PHP official? After googling in the Internet, I found out the followings.
Is this ShellShock’s side effect? Of course, it’s just my joking. But, what happened really? They withdrew the PHP 5.6.1 Zip, which means the file was affected by something malicious?
When I install new files, I always check them up carefully. About the PHP 5.6.1 Zip, I did ordinary steps. However, I do check it up again. In my case, I think that is no problem but who can say it is 100% safe?
They say nothing until now. When do they make the official announcement about it?
Edit(Oct.2):
Now 2:05pm JST, I found the PHP 5.6.1 Zip had come back. I don’t check the difference between the old and new Zip files. I have to get going, so I’ll check them up later. The official still makes no announcement.
ShellShock, shock shock shock!
Whew!!
Have you coped with the threat from ShellShock, yet? My server is on Windows OS. Hence I think the vulnerability gives no effect to mine. But it’s a very serious one. NVD gave the impact score 10 to this. I have a CentOS 6.5 on my VMware, so I updated its bash to bash-4.1.2-15.el6_5.2.i686.
If you still have the following messages after updating and doing env x='() { :;}; echo, your bash need more updating.
vulnerable' bash -c "echo this is a test"
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for 'x'
this is a test
I got the information form Masanari Iida’s comment on Red Hat Customer Portal.
Several links which I am curious about, actually tons of articles about it on the Internet:
- CVE-2014-6271 ⇒ CVE-2014-7169 ⇒ CVE-2014-6277 ⇒ CVE-2014-6278
- Vulnerability Summary for CVE-2014-6271
- Bash ‘shellshock’ scan of the Internet
- Bash Code Injection Vulnerability via Specially Crafted Environment Variables (CVE-2014-6271, CVE-2014-7169)
- GNU bash の脆弱性に関する注意喚起
- GNU bash の脆弱性 ~ shellshock 問題~ について (with animation gifs)
- Shellshock Vulnerability Used in Botnet Attacks
- Bash bug: apply Florian’s patch now (CVE-2014-6277 and CVE-2014-6278)
- ファイアウォール内のサーバに対するShellshockを利用した攻撃
By the way, I had the ShellShock attacks six times and blocked their IPs until yesterday, and today two more from other IPs until now on the Apache error log. I found that all of them my Apache returned HTTP Error Codes to.
Edit(Sep.30):
On “Bash bug: apply Florian’s patch now” he said “I very strongly recommend manually deploying Florian’s patch unless your distro is already shipping it.” and how to check the patch applied or not.
When you do foo='() { echo not patched; }' bash -c foo within the shell, the patch is already applied if you have “command not found”. If you have “not patched”, your bash is still vulnerable.
On its comment vdp wrote “These ‘toughen the feature’ patches still feel quite scary.” and a suggestion. I agree with him.
Edit2Oct.6):
Today, I’ve found this (Japanese).
Woooo!
It says that it’s not enough to check the bash by the code foo='() { echo not patched; }'. Nonetheless, they have less critical than CVE-2014-6271 or CVE-2014-7169. But still dangerous.
bash -c foo
Updating to PHP5.6.1.
They released PHP5.6.1 Windows version on Sep-25 06:28:30UTC. Recently, Windows versions release earlier than other versions. So, I updated my PHP from 5.6.0 to 5.6.1 on my Web server (Windows7HP+SP1(x86)).
There is no difference between the two php.ini-production files except a misspelling correction. So I replaced all files and copied my php.ini file to the folder. Then I restarted the httpd.exe.
About OPcache bug is still remaining. But the above is my ordinary steps. So I thought “That’s it.”
Buuuuuuuuuuuuuuuuuut I had very troubles at this time. First I found the warning “PHP Startup: in Unknown on line 0” on the Apache error log. Only this. It had no module name or anything else. But it was just a warning, i.e. that was a very little problem. And when I checked up the PHP information about PHP Version 5.6.1, I found out the php_curl.dll was not loaded. Boo-hoo-hoo!
Finally I found out the solution after hard work for all day.
I added “x:PHP install directory” to PATH Environment Variable. I think, usually, most of PHP users added it when they first installed PHP. But I didn’t and I had no problem until today. I guessed this is the new requirement of PHP5.6.1 at the first time. However, after reading “the curl extension doesn’t load using apache” and seeing its date, I bet that this trouble maybe depends on Windows Security updates.
Anyway, PHP5.6.1 is working well on the server.
If you need more information for the configuration, see the post “Migrating from PHP 5.5.16 to PHP 5.6.0 on Windows“.
Continued from my last post.
At this post I’ll write ‘How to use SHOUTcast radio’. Of course not about SHOUTcast public radios but about our private radios.
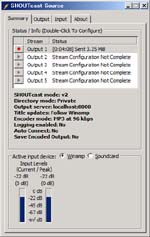
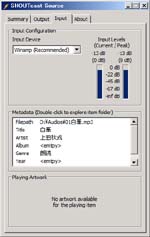
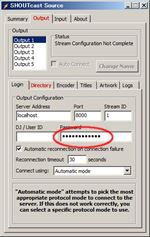
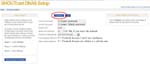
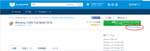
When you just finished ‘Series Net Radio #2‘, your sever is running and your DSP plug-in is connecting with the server. Now play an audio file on the Winamp like the right figure ‘Playing’. Then confirm the status by the browser with accessing to http://localhost:8000 on the server PC (See fig. Status). If accessing from a PC except the sever PC on your Lan, change ‘localhost’ to ‘server_local_ip’. If accessing from a PC in somewhere on the Internet, change ‘localhost’ to ‘server_global_ip’, of course before that you need a correct setting for accessing your server from the Internet.
Let’s try and listen the Net Radio by a player, something like Windows Media Player, Winamp and so on.
You can listen to it on the server PC itself, however, on it you hear both source sounds and client sounds. So, it is better that you try and listen this work on another PC.
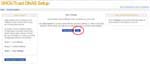
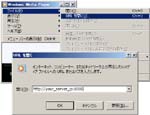
Run Windows Media Player and hit [Alt]key. Then ‘File’ >> ‘Open URL…’. You reach the left figure ‘Open URL’, input URL and click ‘OK’. Can you hear the radio?
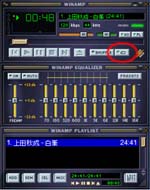
See the figure ‘Playing’ that has a red circle. The icon in the circle is for ‘Loop’. Winamp automatically repeats the audio file when ‘Loop’ sets to ‘ON’. If you set multiple audio files to the Winamp, it plays all files continuously. If you set four files and ‘Loop’ to ‘ON’, the Winamp repeats endlessly, like this: 1 → 2 → 3 → 4 → 1 → 2 → 3 → 4 → 1 → …

My current radio you can listen to on browsers. I embed players in my Net Radio page (It doesn’t exist anymore – 2016.Jun.1) I use HTML5 now, so the codes are very simple. Like this:
<audio controls="controls">
<source src="http://your_sever_ip:8000">
<!-- fallback -->
Your browser cannot handle HTML5.
</audio>
See my Net Radio page (It doesn’t exist anymore – 2016.Jun.1), and you’ll notice that multiple channels exist there. I am running four channels and each channel is putting each reading on the air. When the current server was configured, ‘Allow multiple instances’ was checked. So, you can set at least five streams with DSP plug-in easily. See the right figure ‘Multi-Instances’. Output1 ~ Output4 have the same settings except their Stream_ID.
For listening each stream, you can use next URL formats.
http://your_sever_ip:8000/listen.pls?sid=Stream_ID
http://your_sever_ip:8000/listen.m3u?sid=Stream_ID
http://your_sever_ip:8000/listen.xspf?sid=Stream_ID
http://your_sever_ip:8000/stream/Stream_ID/
But the format http://your_sever_ip:8000/stream/Stream_ID/ is better when you embed it in browsers. Because other than that show errors in environments even if the browsers can handle HTML5.
That’s it for this topic. Very long!! I got tired (^_^;).
Continued from my last post.
My Net Radio station runs with the following formation on Windows(x86), so I install Winamp and SHOUTcast Source DSP now.
| Winamp + DSP (Source) |
<> | DNAS [sc_serv] (Server) |
<> | Something like Players (Client) |
I’d forgotten to write it. DNAS is short for Distributed Network Audio Server and DSP is short for Digital Signal Processing.
| ||How to install Winamp|| | 1. Download | 2. Install | 5. Setting |
| ||How to install DSP|| | 3. Download | 4. Install | 5. Setting |
-
Winamp download Download the latest version of Winamp. Don’t click ‘Download latest version’ but ‘Direct Download’.
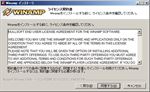
- Installing WinampSelect the language for the install navigation (See fig. Winamp install#1).
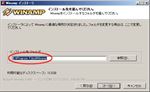
Install Winamp to the default location (See fig. Winamp install#4).Select the install type ‘Lite’ because of this Winamp used for SHOTcast source only and check ‘MP3 encoding’ which exists at Audio Encoders in Multimedia Engine (See fig. Winamp install#5). You can select the language for Winamp at this step if you need.
At Winamp install#6 I uncheck two options but it’s OK if you leave the default.
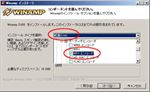
After Winamp install#8 Winamp runs. Close it.‘Control Panel’ >> ‘Administrative Tools’ >> ‘Windows Firewall with Advanced Security’
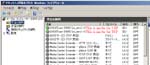
Select ‘Inbound Rules’.You see two rules about Winamp that has a private profile. One is for UDP and another is for TCP. I think they’re not necessary for SHOTcast source features so I delete them (See fig. Winamp install#9).
- Download SHOUTcast Source DSP (shoutcast-dsp-x-x-x-windows.exe) from the same location about SHOUTcast DNAS. Even if you want free version of SHOUTcast DNAS software, to download the files from the official site you need a personal data registration now, like this. (2016.Jun.1)
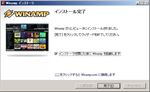
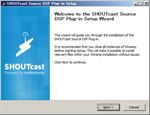
- SHOUTcast Source DSP install.Installing SHOUTcast Source DSP by the default. If you change the Winamp install folder, you have to install your SHOUTcast Source DSP into it.
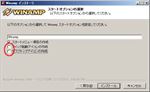
- After ‘DSP install#5’ both Winamp and DSP run.Settings about Winamp itself, ‘Options’ >> ‘Preferences’ (See fig. DSP setting#1).
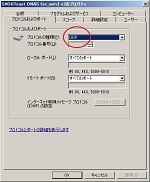
In General Preferences check ‘Allow multiple instances’ and ‘Notification area’. When ‘Allow multiple instances’ is checked, you can broadcast at least five streams by SHOUTcast Source DSP (See fig. DSP setting#2).
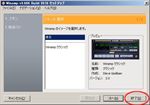
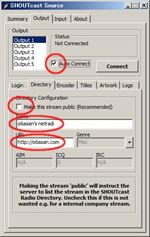
And then close ‘Preferences’.About SHOUTcast Source, set the password (= password in your sc_serv.conf) (See fig. DSP setting#3). Uncheck ‘Make this stream public’ because the current server is a private one. Change ‘Name’ and ‘URL’ to your own. Then check ‘Auto Connect’ or click ‘Connect’.
Now the preparation for the broadcast is completed. You make the Winamp play an audio, and the broadcasting will start.
If you want to use the radio within your LAN only, you can already do it. But if you want to give your service to someone on the Internet and use a router or something, you’ll need to set them up. About it see your router manual or ask your network admin.
The next post I will write how to use the SHOUTcast radio.
It was on 2011 October 13 that I wrote the first article about Net Radio. One of my Japanese blog visitors consulted with me as to begin a net radio station, so I learned and created my private net radio station(It doesn’t exist anymore – 2016.Jun.1) though I didn’t know anything about it at the time. The station was only for me and the situation is the same still now. Anyway I have a net radio station and am using SHOUTcast DNAS for it.
Last year AOL decided to sell SHOUTcast and Winamp and Radionomy bought SHOUTcast on 2014 January 14. Hence, I will write a new article about SHOUTcast private radio. Shall I start?
| ||How to create a SHOUTcast server|| | ||
| 1. Download 4. Install as a Service |
2. Install 5. Firewall |
3. Setup 6. Login test |
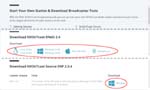
- Download SHOUTcast DNAS from here. Even if you want free version of SHOUTcast DNAS software, to download the files from the official site you need a personal data registration now, like this. (2016.Jun.1) Click ‘DOWNLOAD’ then you can see the links for download.
About SHOUTcast DNAS, you have to download a correct version. In my case, I downloaded sc_serv2_win32_xx_xx_xxxx.exe.
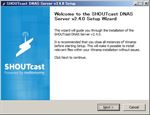
- Install sc_serv2_win32_xx_xx_xxxx.exe
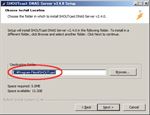
If you install DNAS to the default folder, you have the message of ‘SHOUTcast install#4’ image. In most cases you’d better click ‘No’ and change the install folder from the default, for example D:SHOUTcast.
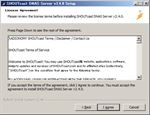
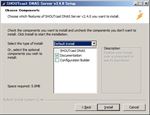
When you click ‘Finish’, SHOUTcast shows you ‘Readme_DNAS_Server.html’ by your browser. So, read ‘Getting Started’ first. - Setup SHOUTcast DNAS Server.
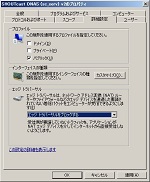
You have a Windows Security Alert about SHOUTcast DNAS, then allow access about public networks only (See fig. SHOUTcast setup#1). I don’t have exact knowledge about Public, Private and Domain settings, but I feel better that to allow access is only for Public as I read Understanding Firewall Profiles.
Run cmd.exe as Administrator and move to SHOUTcast folder which includes ‘setup.bat’.
Run setup.bat on cmd.
> setup.bat
You have a setup page on your browser like the followings (See figs. SHOUTcast setup#2 ~ #4):See the above images and do the settings.
Close your browser.
Now you have a conf file named ‘sc_serv.conf’ in the SHOUTcast folder. This is the default conf for the server.The text of sc_serv.conf:
adminpassword=(your existing adminpassword)Because the current server is private.
autoauthhash=0
maxuser=20If the default value, it’s maybe OK.
password=(your existing password)
publicserver=never
streamid_1=1
Here are the passwords. The passwords themselves are clear text. For security purposes, I STRONGLY recommend that you don’t use passwords that are used to access critical system components or other sensitive information. Make these as random as possible, with a combination of letters, numbers and symbols. - Install as a Service
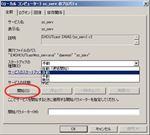
Service setting
On the cmd:
> sc_serv.exe install sc_serv
Close the cmd.exe.
‘Control Panel’ >> ‘Administrative Tools’ >> ‘Services’
Select sc_serv and change its startup type value to ‘Automatic’. Click ‘Start’ and ‘OK’.
If you need more information, see ‘DNAS_Server.html#Install_as_a_Service’ in the SHOUTcastdocs. - Setting firewall for SHOUTcast DNAS.
‘Control Panel’ >> ‘Administrative Tools’ >> ‘Windows Firewall with Advanced Security’
Select ‘Inbound Rules’.
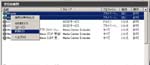
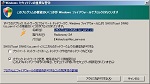
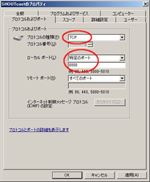
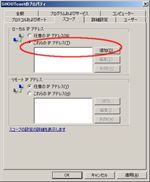
You see two rules about SHOUTcast DNAS (sc_serv) v2 that has public profile, if your step was normally done at ‘SHOUTcast setup#1’. One is for UDP and another is for TCP. You don’t need to open UDP ports, so delete the UDP rule. (See figs. Firewall settings#1 & #2)
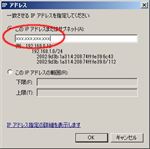
Change the following values about TCP rule (See figs. Specific Ports 8000 ~ Advanced, Block edge traversal):Click ‘OK’.
- Login test.
You can log in the server by your adminpassword.
Access http://your_server_ip:8000 (the default: http://localhost:8000), then you’ll have ‘SHOUTcast Server Summary’ by the browser.
To create a SHOUTcast server is complete!! The next post I will write the installations about Winamp and SHOUTcast DSP.
Hi guys! Do you know Meiwa Denki (明和電機)? That is the Meiwa Denki whose performances I love. Their performances you can see on YOUTUBE and here is the video that BBC introduces them.
Mr.Knocky, I rolled on the floor laughing for the first time in several months. 土佐さん is always a genius, don’t you think so? (^_~)
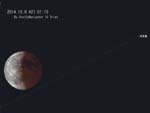
Tonight is “Otsukimi”, but cloudy.
Tonight is “Otsukimi“. Yesterday, I had very clear moon, but cloudy tonight (around 21:00).
We have a folklore that says a rabbit lives on the moon and it pounds mochi. A song for you about rabbits and the moon. I apologize for the noise in advance. After upgrading to Windows 8.1, I cannot use a genuine sound driver for NJ2100. The noise maybe depends on it.
- うさぎ (Rabbit)
Usaki, usaki, nani mite haneru.
うさぎ,うさぎ,なに見てはねる。
Jūgoya otsuki sama, mite haneru.
十五夜お月さま,見てはねる。
Now, I can see beautiful Full Moon. But, almost Sep 9.