Update information Edit Edit2(Jul.7) Edit3(Sep.2)
Yesterday, I came home around 8 pm and saw the first fireflies of this year in my garden. Wow!
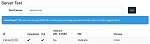 By the way, I read the article “TLSに脆弱性「Logjam」 – 国家レベルなら1024ビットまで盗聴可能” on May 21. Then I went to Guide to Deploying Diffie-Hellman for TLS and did Server Test. I got the result like the right image. Before the test, despite I didn’t do anything else more than I had done until 2014.Oct.28 (= A self-sighed certificate with SANs and SHA256 by OpenSSL).
By the way, I read the article “TLSに脆弱性「Logjam」 – 国家レベルなら1024ビットまで盗聴可能” on May 21. Then I went to Guide to Deploying Diffie-Hellman for TLS and did Server Test. I got the result like the right image. Before the test, despite I didn’t do anything else more than I had done until 2014.Oct.28 (= A self-sighed certificate with SANs and SHA256 by OpenSSL).
And that night, I had a comment from くりくりさん on my Japanese blog. He let me know about Logjam. I wrote back him that I tried writing about Logjam and I’m writing it now, ha-ha.
When I tested my server at the first time, the server supported the following Cipher Suites.
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-CBC-SHA384
- ECDHE-RSA-AES128-CBC-SHA256
- ECDHE-RSA-AES256-CBC-SHA
- ECDHE-RSA-AES128-CBC-SHA
- DHE-RSA-AES256-GCM-SHA384
- DHE-RSA-AES256-CBC-SHA256
- DHE-RSA-AES256-CBC-SHA
- DHE-RSA-CAMELLIA256-CBC-SHA
- DHE-RSA-AES128-GCM-SHA256
- DHE-RSA-AES128-CBC-SHA256
- DHE-RSA-AES128-CBC-SHA
- DHE-RSA-SEED-CBC-SHA
- DHE-RSA-CAMELLIA128-CBC-SHA
But actually I don’t need most of them. Because the user of my SSL server is only me and I usually use the latest version Web Browsers as I always say. I only use ECDHE-RSA-AES128-GCM-SHA256 suite at my access. So I changed SSLCipherSuite directive on my ssl.conf like this.
SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256
This configuration is not useful for other servers. If you want to know a realistic configuration, see Guide to Deploying Diffie-Hellman for TLS. If your server is in newer versions of Apache (2.4.8 and newer) and OpenSSL 1.0.2 or later, you can directly specify your DH params file. But even if your server isn’t, you can use SSLCipherSuite and SSLProtocol instead of SSLOpenSSLConfCmd and can make your server safe from Logjam attack.
 Actually, ApacheLounge version HTTPD is still built with OpenSSL 1.0.1 branch. So I could not use SSLOpenSSLConfCmd directive. But after changing my SSLCipherSuite, I got the result like right image.
Actually, ApacheLounge version HTTPD is still built with OpenSSL 1.0.1 branch. So I could not use SSLOpenSSLConfCmd directive. But after changing my SSLCipherSuite, I got the result like right image.
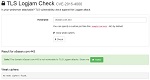 Another Logjam Attack Checker gave me the right result.
Another Logjam Attack Checker gave me the right result.
In addition, when using Apache 2.4 with OpenSSL 1.0.1 and later, SSLProtocol all means +SSLv3 +TLSv1 +TLSv1.1 +TLSv1.2. When using Apache 2.4.7 or later, aNULL, eNULL and EXP ciphers are always disabled.
Edit:
According to the The Logjam Attack page, Google Chrome (including Android Browser), Mozilla Firefox, Microsoft Internet Explorer, and Apple Safari are all deploying fixes for the Logjam attack. But still now (9:45 am JST), I have Warning! Your web browser is vulnerable to Logjam and can be tricked into using weak encryption. You should update your browser when I access the page by FireFox 38.0.1, Google Chrome 43.0.2357.65 or SeaMonkey 2.33.1. Only Internet Explorer 11.0.19 gives Good News! Your browser is safe against the Logjam attack.
Note) I don’t check this with other browsers and versions.
Edit2(Jul.7):
Yesterday, FireFox 39.0 came. Now I have Good News! Your browser is safe against the Logjam attack by it.
Edit3(Sep.2):
I’ve not checked it for a while. Today, Google Chrome ver. 45.0.2454.85 has come, so I check just now. The site gives Good News! Your browser is safe against the Logjam attack. When was Chrome deploying fixes for it? I have no idea!!
Edit(Sep.5):
Now 1:00a.m. SeaMonkey’s new version 2.35 has come after long interval. And, I’ve finally had Good News! Your browser is safe against the Logjam attack by it.
