Continued from this post. As I finished preparing for supporting HTTP/2, I re-edited my httpd.conf and httpd-ssl.conf.
On the httpd.conf, I un-commented the next line.
LoadModule http2_module modules/mod_http2.so
On the httpd-ssl.conf, I added the next line just after <VirtualHost o6asan.com:443>.
Protocols h2 http/1.1
h2 is HTTP/2 with TLS and h2c is HTTP/2 without TLS. I don’t use h2c on the server.
Reboot Apache to enable Http/2. That’s it.
Tag: WebServer
Memorandum #13.
Being too busy with writing HTTP/2, I’ll also write about it, which is I moved to MariaDB 10.1.8. Not to update it. Besides, I found PHP5.6.15, phpMyAdmin4.5.1 and ActivePerl-5.20.2.2002 yesterday, so I took care of them all.
They released Apache 2.4.17 on Oct 13 and Steffen released the same version at ApacheLounge on Oct 12. The version has mod_http2 for its core module and Steffen’s version was built with nghttp2 v1.3.4. See ChangeLog. So, I can test HTTP/2 on my server now. Yes! Just test. Because they say “This module is experimental.”
phpMyAdmin 4.5.0 is released.
They released phpMyAdmin 4.5.0.0 on September 23, 4.5.0.1 on September 24 and 4.5.0.2 on September 25. What new releases in sequence! Ha-ha!! Here is the ChangeLogs. The 4.5.0.0 has a tons of improvements by RFE(Request for enhancement) or so. The 4.5.0.1 and 4.5.0.2 are bugfix versions.
Memorandum #12.
I updated my Apache 2.4.12(httpd-2.4.12-win32-VC14.zip) to 2015 Jul 9 version because of Alternative chains certificate forgery (CVE-2015-1793).
It is built with ‘IPv6 Crypto apr-1.5.1 apr-util-1.5.4 apr-iconv-1.2.1 openssl-1.0.2d zlib-1.2.8 pcre-8.37 libxml2-2.9.2 lua-5.1.5 expat-2.1.0′. Its Changelog.
This version is also built with the latest Windows® Visual Studio C++ 2015 RC aka VC14. I began to use VC14 version on June 2 due to OpenSSL 1.0.2. If you use the version, you need to install vc_redist_x64/86.exe before installing the version.
I really appreciate Steffen’s hard and quick work. Thanks again, Steffen.
By the way, I take this occasion to update to phpMyAdmin 4.4.11 and MariaDB 10.0.20.
About phpMyAdmin I noticed two differences. From the version 4.4.10 the download URL changed from sourceforge.net to phpmyadmin.net. And this version, I mean 4.4.11, they provide not only MD5/SHA1 but PGP. I wonder if something happened between sourceforge and phpmyadmin.
Although belated, about Logjam.
Yesterday, I came home around 8 pm and saw the first fireflies of this year in my garden. Wow!
![]() By the way, I read the article “TLSに脆弱性「Logjam」 – 国家レベルなら1024ビットまで盗聴可能” on May 21. Then I went to Guide to Deploying Diffie-Hellman for TLS and did Server Test. I got the result like the right image. Before the test, despite I didn’t do anything else more than I had done until 2014.Oct.28 (= A self-sighed certificate with SANs and SHA256 by OpenSSL).
By the way, I read the article “TLSに脆弱性「Logjam」 – 国家レベルなら1024ビットまで盗聴可能” on May 21. Then I went to Guide to Deploying Diffie-Hellman for TLS and did Server Test. I got the result like the right image. Before the test, despite I didn’t do anything else more than I had done until 2014.Oct.28 (= A self-sighed certificate with SANs and SHA256 by OpenSSL).
And that night, I had a comment from くりくりさん on my Japanese blog. He let me know about Logjam. I wrote back him that I tried writing about Logjam and I’m writing it now, ha-ha.
When I tested my server at the first time, the server supported the following Cipher Suites.
- ECDHE-RSA-AES256-GCM-SHA384
- ECDHE-RSA-AES128-GCM-SHA256
- ECDHE-RSA-AES256-CBC-SHA384
- ECDHE-RSA-AES128-CBC-SHA256
- ECDHE-RSA-AES256-CBC-SHA
- ECDHE-RSA-AES128-CBC-SHA
- DHE-RSA-AES256-GCM-SHA384
- DHE-RSA-AES256-CBC-SHA256
- DHE-RSA-AES256-CBC-SHA
- DHE-RSA-CAMELLIA256-CBC-SHA
- DHE-RSA-AES128-GCM-SHA256
- DHE-RSA-AES128-CBC-SHA256
- DHE-RSA-AES128-CBC-SHA
- DHE-RSA-SEED-CBC-SHA
- DHE-RSA-CAMELLIA128-CBC-SHA
But actually I don’t need most of them. Because the user of my SSL server is only me and I usually use the latest version Web Browsers as I always say. I only use ECDHE-RSA-AES128-GCM-SHA256 suite at my access. So I changed SSLCipherSuite directive on my ssl.conf like this.
SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256
This configuration is not useful for other servers. If you want to know a realistic configuration, see Guide to Deploying Diffie-Hellman for TLS. If your server is in newer versions of Apache (2.4.8 and newer) and OpenSSL 1.0.2 or later, you can directly specify your DH params file. But even if your server isn’t, you can use SSLCipherSuite and SSLProtocol instead of SSLOpenSSLConfCmd and can make your server safe from Logjam attack.
![]() Actually, ApacheLounge version HTTPD is still built with OpenSSL 1.0.1 branch. So I could not use SSLOpenSSLConfCmd directive. But after changing my SSLCipherSuite, I got the result like right image.
Actually, ApacheLounge version HTTPD is still built with OpenSSL 1.0.1 branch. So I could not use SSLOpenSSLConfCmd directive. But after changing my SSLCipherSuite, I got the result like right image.
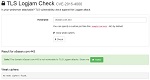 Another Logjam Attack Checker gave me the right result.
Another Logjam Attack Checker gave me the right result.
In addition, when using Apache 2.4 with OpenSSL 1.0.1 and later, SSLProtocol all means +SSLv3 +TLSv1 +TLSv1.1 +TLSv1.2. When using Apache 2.4.7 or later, aNULL, eNULL and EXP ciphers are always disabled.
Edit:
According to the The Logjam Attack page, Google Chrome (including Android Browser), Mozilla Firefox, Microsoft Internet Explorer, and Apple Safari are all deploying fixes for the Logjam attack. But still now (9:45 am JST), I have Warning! Your web browser is vulnerable to Logjam and can be tricked into using weak encryption. You should update your browser when I access the page by FireFox 38.0.1, Google Chrome 43.0.2357.65 or SeaMonkey 2.33.1. Only Internet Explorer 11.0.19 gives Good News! Your browser is safe against the Logjam attack.
Note) I don’t check this with other browsers and versions.
Edit2(Jul.7):
Yesterday, FireFox 39.0 came. Now I have Good News! Your browser is safe against the Logjam attack by it.
Edit3(Sep.2):
I’ve not checked it for a while. Today, Google Chrome ver. 45.0.2454.85 has come, so I check just now. The site gives Good News! Your browser is safe against the Logjam attack. When was Chrome deploying fixes for it? I have no idea!!
Edit(Sep.5):
Now 1:00a.m. SeaMonkey’s new version 2.35 has come after long interval. And, I’ve finally had Good News! Your browser is safe against the Logjam attack by it.
Memorandum #11.
I’ve updated some server software on my Web server (The server OS is Win7 HP SP1 x86).
- MariaDB 10.0.17 —->> MariaDB 10.0.19 (Changelog)
- PHP 5.6.8 —->> PHP 5.6.9 (Changelog)
- phpMyAdmin 4.4.6 —->> phpMyAdmin 4.4.7 (Changelog)
- sc_serv2_win32_09_09_2014.exe —->> sc_serv2_win32-latest.exe (Ver. 2.4.7)
shoutcast-dsp-2-3-4-windows.exe —->> shoutcast-dsp-2-3-5-windows.exe
Note) To download the files you need a valid email address. Even if you want free version of SHOUTcast DNAS software, to download the files from the official site you need a personal data registration now, like this. (2016.Jun.1)
Memorandum #10.
I’ve updated some server software on my Web server (The server OS is Win7 HP SP1 x86).
- MariaDB 10.0.16 —->> MariaDB 10.0.17 (Changelog)
- PHP 5.6.7 —->> PHP 5.6.8 (Changelog)
Note) They created new directory lib under <php_root>. This is related to the bug #65406. - phpMyAdmin 4.3.10 —->> phpMyAdmin 4.4.3 (Changelog)
Note) They deleted the following lines from the new config.sample.inc.php.- * default display direction (horizontal|vertical|horizontalflipped)
*/
//$cfg[‘DefaultDisplay’] = ‘vertical’;
/**
- * default display direction (horizontal|vertical|horizontalflipped)
- ActivePerl 5.20.1.2000 —->> ActivePerl 5.20.2.2001
- WordPress 4.1.1 —->> WordPress 4.1.2
Note) This was updated automatically.
Updating to PHP5.6.7.
They released PHP5.6.7 Windows version on Mar-19 23:50:34UTC. It fixes several bugs as well as CVE-2015-0231 (bug #68976), CVE-2015-2305 (bug #69248) and CVE-2015-2331 (bug #69253). The previous version (PHP5.6.5) has a bug fix for CVE-2015-0231, so this bug fix is second time. I wonder if some unfixed issues still remain for this vulnerability. Anyway I updated my PHP from 5.6.6 to 5.6.7 on my Web server (Windows7HP+SP1(x86)).
By the way, the new version includes some fixes for OPcache. But I have no new report on the page Bug #67937. So, nothing might change about it, but I enabled OPcache on my server again (Mar-29@6:55JST). What results will I have? I feel nervous about it.
If you need more information for the configuration, see the post “Migrating from PHP 5.5.16 to PHP 5.6.0 on Windows”.
Edit(Apr.14):
The OPcache on my Windows server has worked well for more than two weeks. I don’t know why. But I am happy!!